快速搭建一个授权服务器零配置
简介
Spring全新认证授权服务 Spring Authorization Server
以下全文 Spring Authorization Server 简称为: SAS
背景
Spring 团队正式宣布停止维护 Spring Security OAuth 项目,该项目将不再进行任何迭代。在 Spring 生态系统中,可以使用 Spring Authorization Server 的 OAuth2 授权服务器,已经可以正式用于生产环境。
SAS 1.1.0 版本中,官方提供了自动化配置的 starter,可以零配置使用 SAS 认证服务器。只需添加以下 Maven 依赖:
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-oauth2-authorization-server</artifactId>
</dependency>此外,还可以在 Spring Initializr 中直接选择使用。当然,必须使用 SpringBoot 3.x。
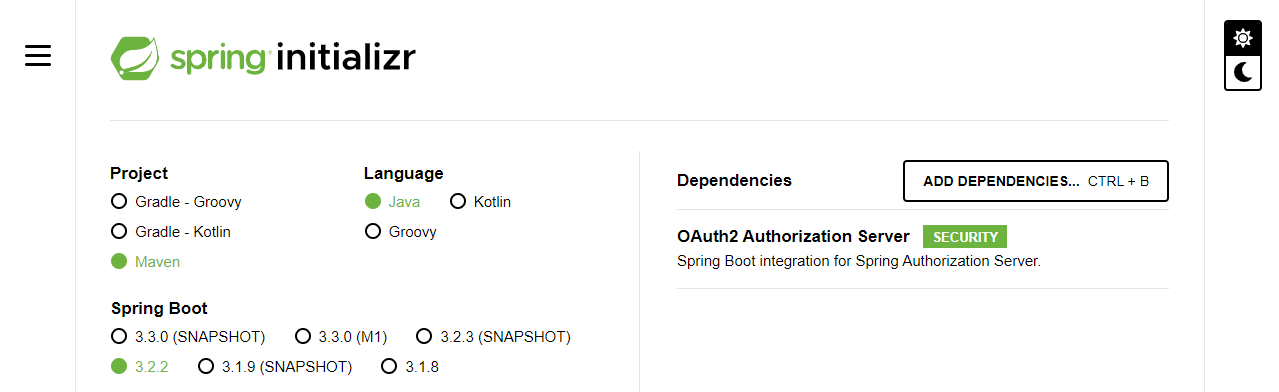
认证服务器搭建
环境:SpringBoot3.2.2 + JDK17
添加依赖
只需要在pom.xml引入 sas starter + web 依赖即可
xml<dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-oauth2-authorization-server</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency>
配置信息
application.yml
yamlserver: port: 9000 logging: level: org.springframework.security: trace spring: security: user: name: user1 password: password oauth2: authorizationserver: client: messaging-client: registration: client-id: "messaging-client" client-secret: "{noop}secret" client-authentication-methods: - "client_secret_basic" authorization-grant-types: - "authorization_code" - "refresh_token" - "client_credentials" redirect-uris: - "http://127.0.0.1:8080/login/oauth2/code/messaging-client-oidc" - "http://127.0.0.1:8080/authorized" - "https://www.pigx.cn" post-logout-redirect-uris: - "http://127.0.0.1:8080/logged-out" scopes: - "openid" - "profile" - "message.read" - "message.write" require-authorization-consent: true
模拟测试
注意
在新版本的sas(1.2.1)中获取token更新了授权码校验逻辑,只能用form-data传递参数,使用url-params会失败,原因见issue1451 对应的 commit 在这里: Fix to ensure endpoints distinguish between form and query parameters
设置Basic Auth
客户端设置的认证方式是CLIENT_SECRET_BASIC,所以需将客户端信息添加至请求头。
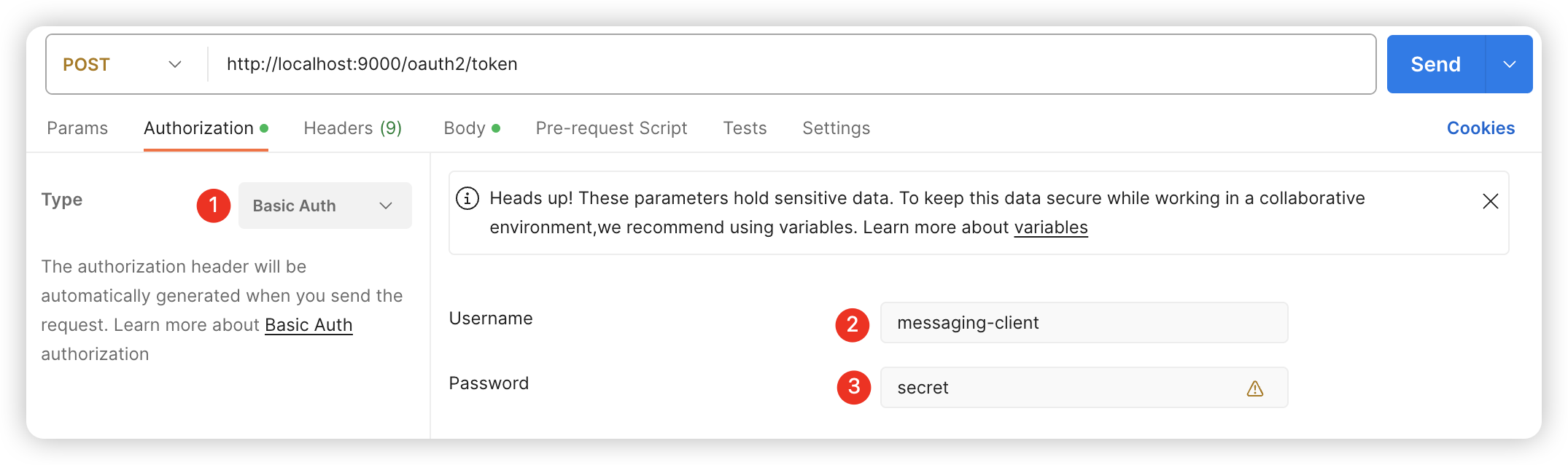
① POST 客户端模式
Postman调试
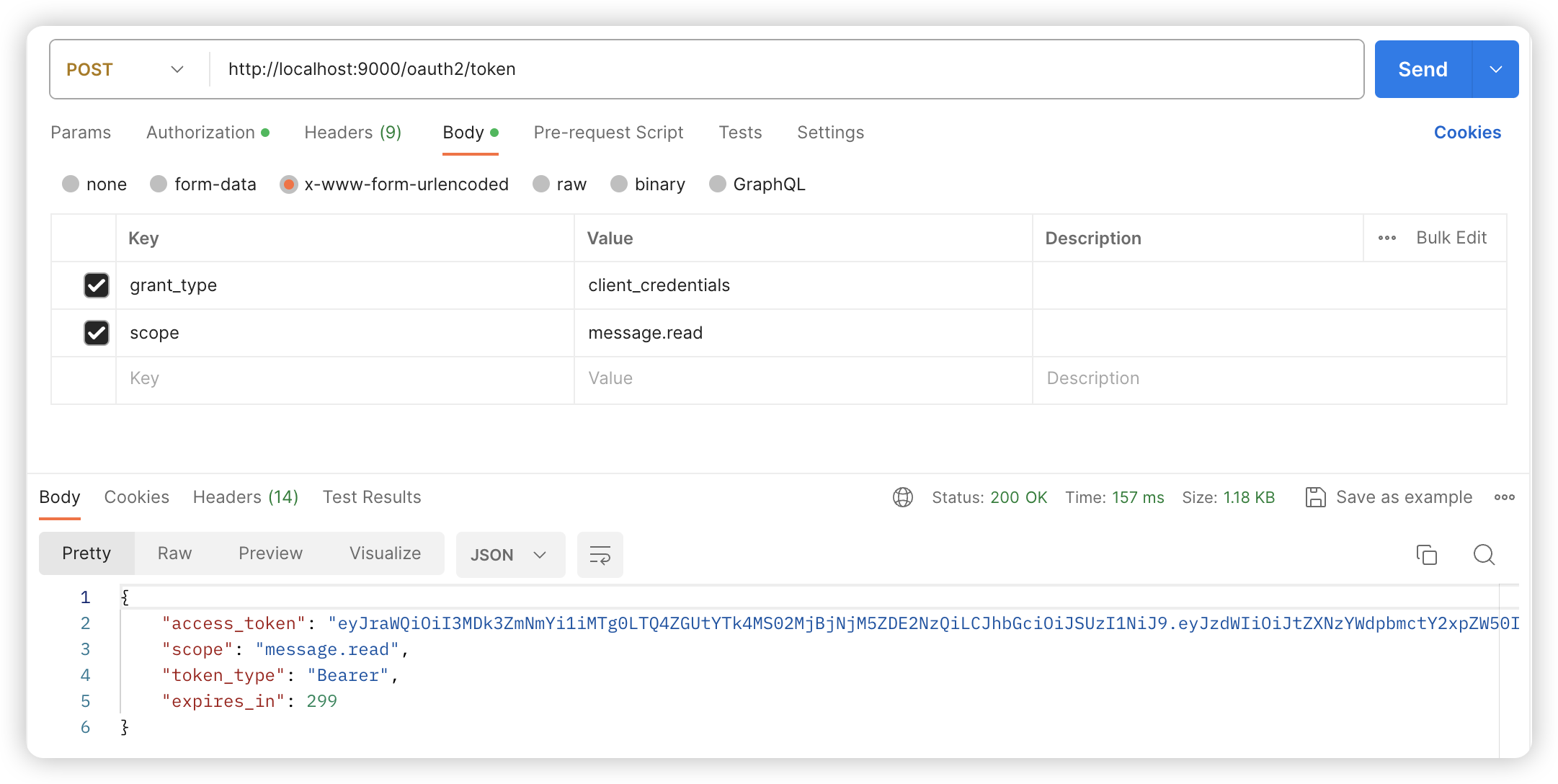
POST /oauth2/token
Body 请求参数
grant_type: client_credentials
scope: message.read请求参数
| 名称 | 位置 | 类型 | 必选 | 说明 |
|---|---|---|---|---|
| body | body | object | 是 | none |
| » grant_type | body | string | 是 | 授权方式客户端模式 |
| » scope | body | string | 否 | scope 域 |
代码片段
curl --location 'http://localhost:9000/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic bWVzc2FnaW5nLWNsaWVudDpzZWNyZXQ=' \
--data-urlencode 'grant_type=client_credentials' \
--data-urlencode 'scope=message.read'请求结果
{
"access_token": "eyJraWQiOiJmYTc0ZTViNi1hYThlLTQ0MDQtOTViOC04YzM1MjEyNTIzYTciLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJtZXNzYWdpbmctY2xpZW50IiwiYXVkIjoibWVzc2FnaW5nLWNsaWVudCIsIm5iZiI6MTcwODQ5Mzc4Nywic2NvcGUiOlsibWVzc2FnZS5yZWFkIl0sImlzcyI6Imh0dHA6Ly9sb2NhbGhvc3Q6OTAwMCIsImV4cCI6MTcwODQ5NDA4NywiaWF0IjoxNzA4NDkzNzg3LCJqdGkiOiI5MDY0MzFhNS1kMmY1LTQxOWYtOTYzMC03MjJjYmNjZmZjMjYifQ.p_2VZruC2DQ9ttcwvQkaO0U2mCpbVoVMn977V5pb9GJEpw5n9ssb4z-_QhxGtGnRRcgpQDMB4CTG4qSbSYmi0AVOOlpTQgrI1NoOZZRN8dfaKM7Ou7l6GRU0568AMe-x-jYtFlgnkZsKfbrXu2XVADPQI8fRfPFLeOdjleOvo-AKQVDYPNHsev2Dh6qup-HZhix5cAaFZpESX_3x3_lU13MhVyGhFLwAE-N0Ns0xDfGsq-qz1HrnAViN7ZC870XGWfKoh0eWUBG1J4278k5t7a3LCkAOQoryYrG_aDcKAxpjxjykitYRs94xDNpAxzOW4tELUSVKofCdJcq2jq7IjQ",
"scope": "message.read",
"token_type": "Bearer",
"expires_in": 299
}② POST 授权码模式
1.拼接url,访问授权接口
授权码获取
http://localhost:9000/oauth2/authorize?response_type=code&client_id=messaging-client&scope=message.read&redirect_uri=https://www.pigx.cn2.授权接口检测到未登录,重定向至登录页面
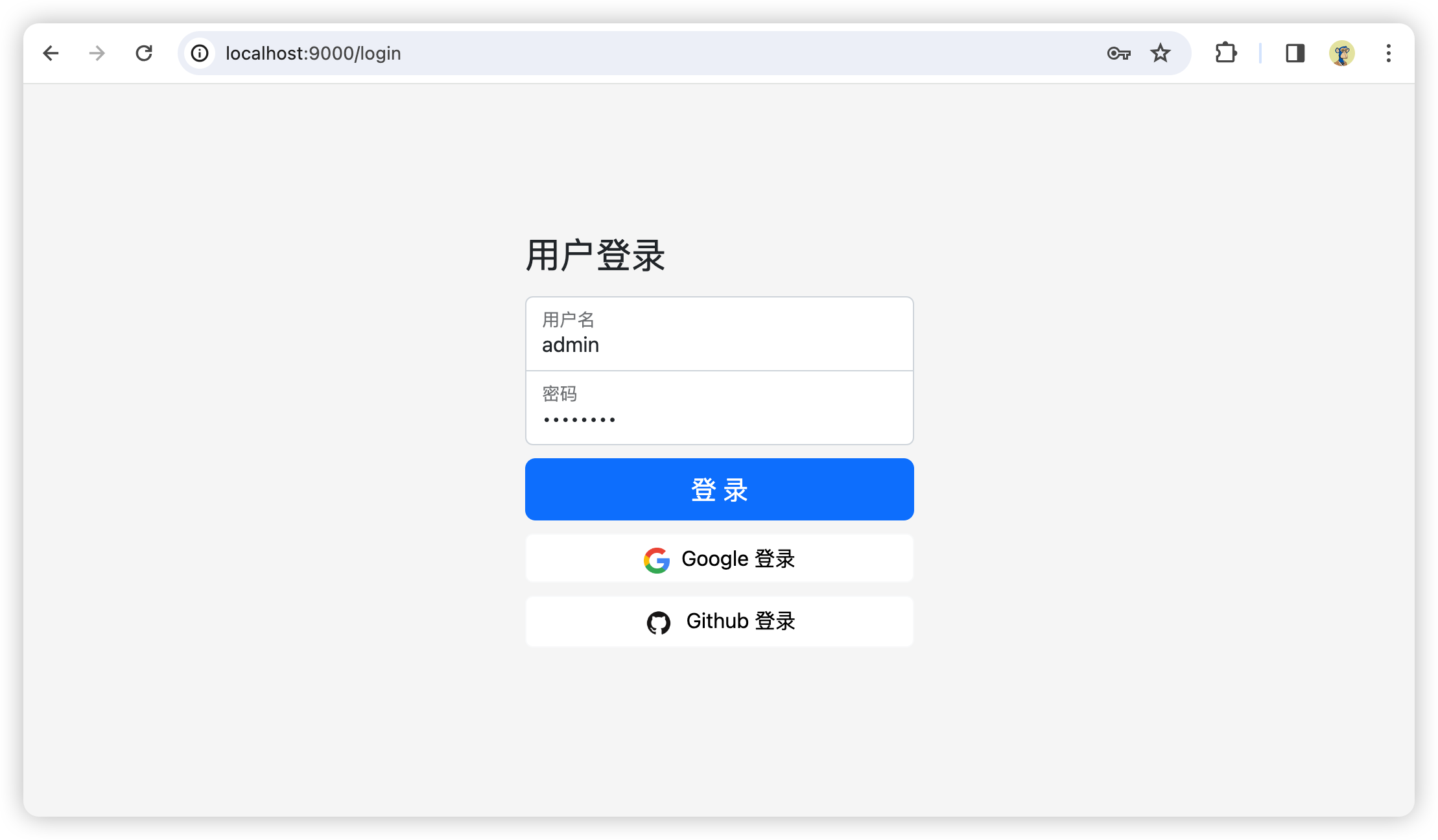
3.输入AuthorizationConfig中配置的账号密码
账号:admin 密码:password
4.登录成功后跳转至授权确认页面
登录成功跳转至第1步的授权接口,授权接口检测到用户未确认授权,跳转至授权确认页面
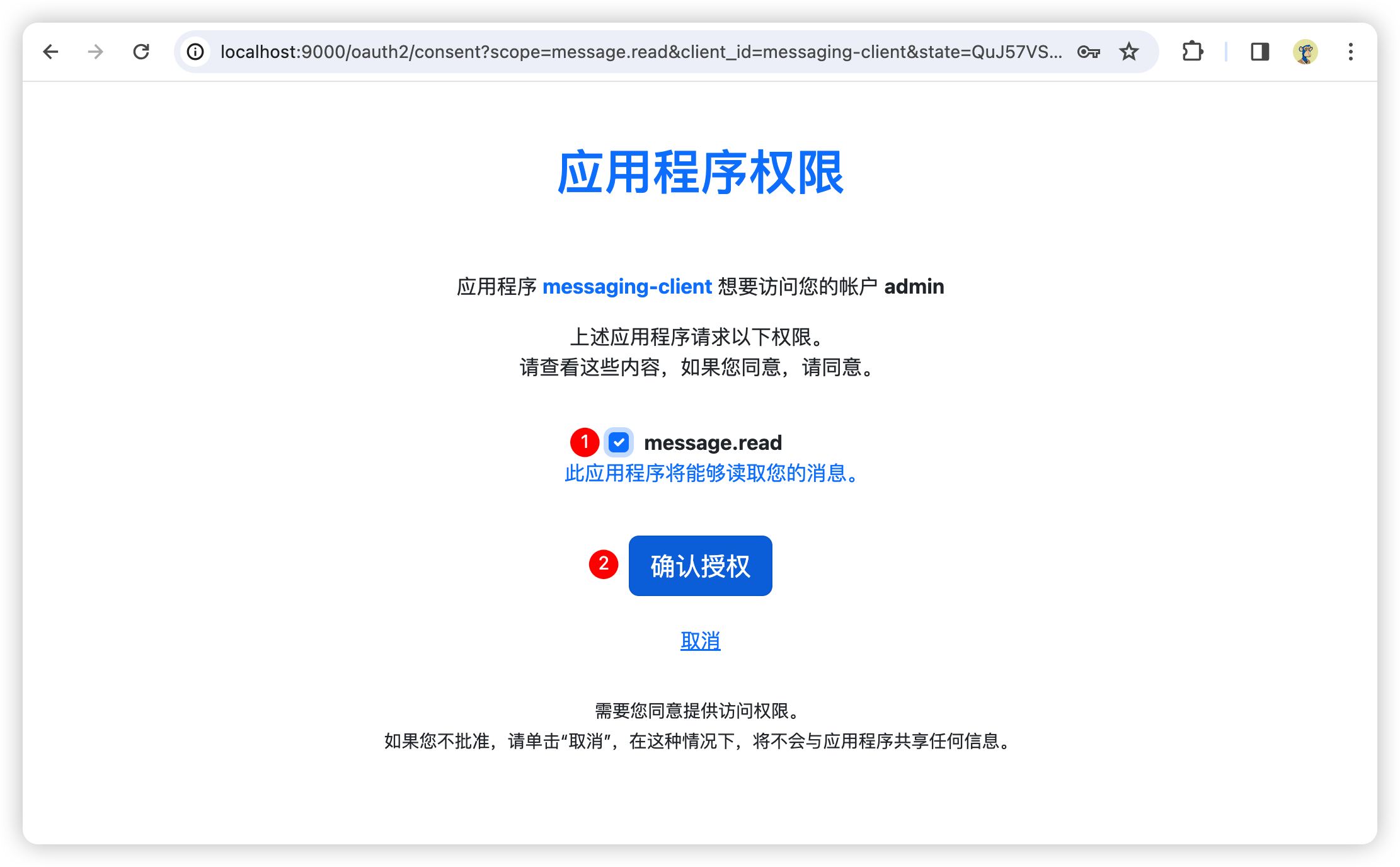
选择对应的scope并提交确认授权
5.提交后重定向至第1步的授权接口
INFO
授权接口生成code并重定向至第1步请求授权接口时携带的redirectUri地址,重定向时携带上参数code和state,我这里省略掉了state参数,重定向之后只会携带code参数;state用来防止CSRF攻击,正式请求需生成并携带state参数。
6.用户确认授权后携带code跳转至redirectUri
INFO
一般来说配置的回调地址都是客户端的接口,接口在接收到回调时根据code去换取accessToken,接下来我会用postman模拟客户端发起一个http请求去换取token
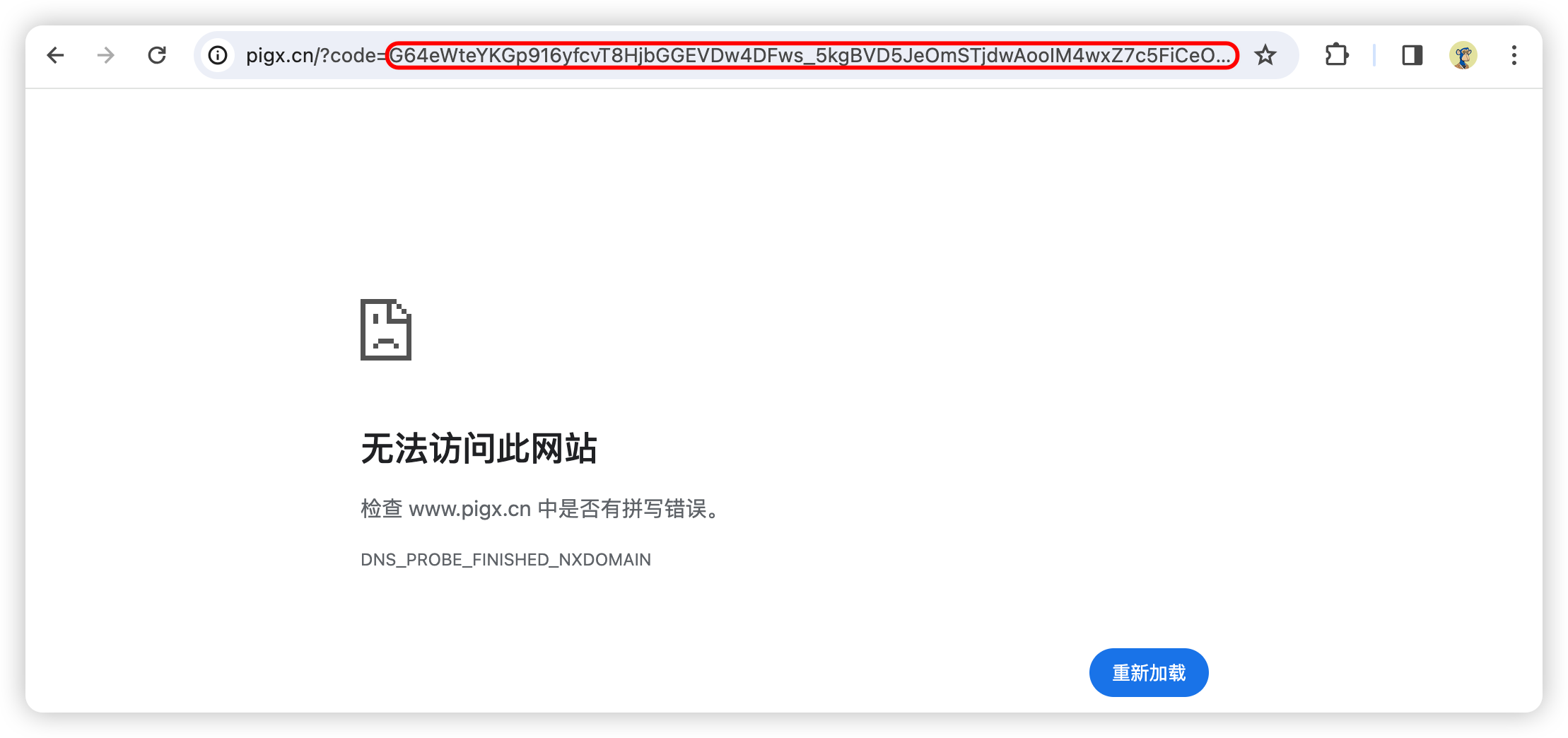
7.根据code换取AccessToken
Postman调试
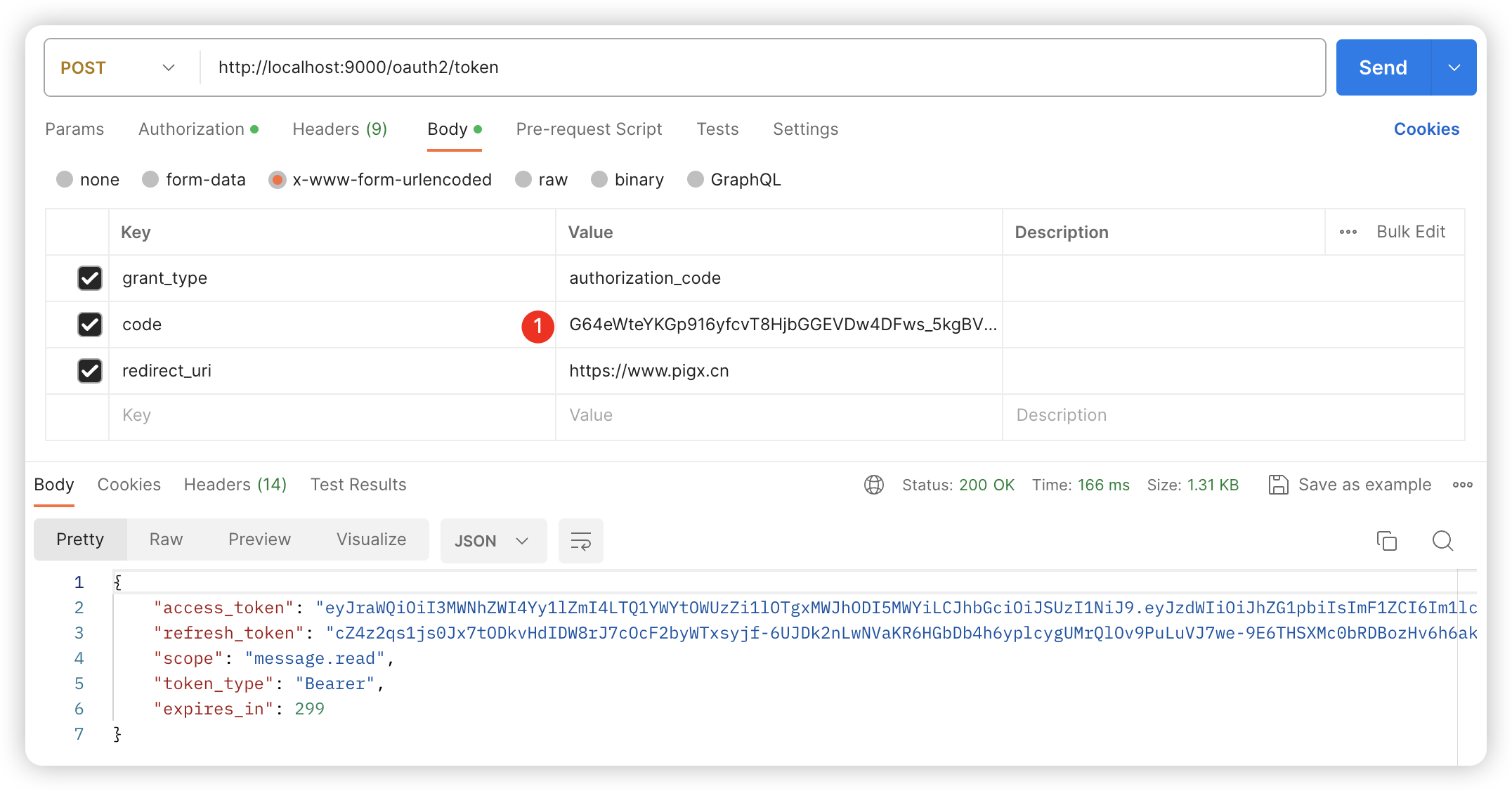
POST /oauth2/token
Body 请求参数
grant_type: authorization_code
code: G64eWteYKGp916yfcvT8HjbGGEVDw4DFws_5kgBVD5JeOmSTjdwAooIM4wxZ7c5FiCeOBu5x0QBPE5bN0BGUd4VYG6PVeU4uSLqxbH3M9w2XrmqGRt0PkRI_ZPJiD5Y5
redirect_uri: https://www.pigx.cn请求参数
| 名称 | 位置 | 类型 | 必选 | 说明 |
|---|---|---|---|---|
| body | body | object | 是 | none |
| » grant_type | body | string | 是 | 授权码模式 |
| » code | body | string | 是 | 授权码 |
| » redirect_uri | body | string | 是 | 回调地址 |
代码片段
curl --location 'http://localhost:9000/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic bWVzc2FnaW5nLWNsaWVudDpzZWNyZXQ=' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'code=G64eWteYKGp916yfcvT8HjbGGEVDw4DFws_5kgBVD5JeOmSTjdwAooIM4wxZ7c5FiCeOBu5x0QBPE5bN0BGUd4VYG6PVeU4uSLqxbH3M9w2XrmqGRt0PkRI_ZPJiD5Y5' \
--data-urlencode 'redirect_uri=https://www.pigx.cn'请求结果
{
"access_token": "eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjY3MTIsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjcwMTIsImlhdCI6MTcwODg2NjcxMiwianRpIjoiOTk2MjI3ZmUtYzQ3ZS00ZWIxLTk2OWQtZGIxMzlkMDA5MDAzIn0.bmo0CyrxjIH7Dzkv4M7BS4PvCrUUyy7CZ9WmIO_LNO3UT3sTiq3MdvAw9MRDr5L2TKMPWhMlf6bZgZSQqF-DEDaiDOQZH0VftDNPQMD4nwL_V1f3GQWn30tkyKzK6MHHb5Xw3qsWsvumWrbekSEUwMtgZkeCnI1jNf-X4BASv3Jgs8V2iKTNZIrsOLSy-zJ8OC7itI9sfJfOnHQfCWwLWL3Rz5_5BCvO_pkOSVnDptyyRGYCc_qH08uXhdO_FJeTh0xa3jxEGZJuvIg-uKgMWNNxXEee6gudPi15ADAhPRRHfrizA89rUiZImFsKT6EwFpxAMl9PPT2QhA4tjGMd7Q",
"refresh_token": "cZ4z2qs1js0Jx7tODkvHdIDW8rJ7cOcF2byWTxsyjf-6UJDk2nLwNVaKR6HGbDb4h6yplcygUMrQlOv9PuLuVJ7we-9E6THSXMc0bRDBozHv6h6akNYFmxDkbwIya_Pq",
"scope": "message.read",
"token_type": "Bearer",
"expires_in": 299
}③ POST 刷新模式
Postman调试
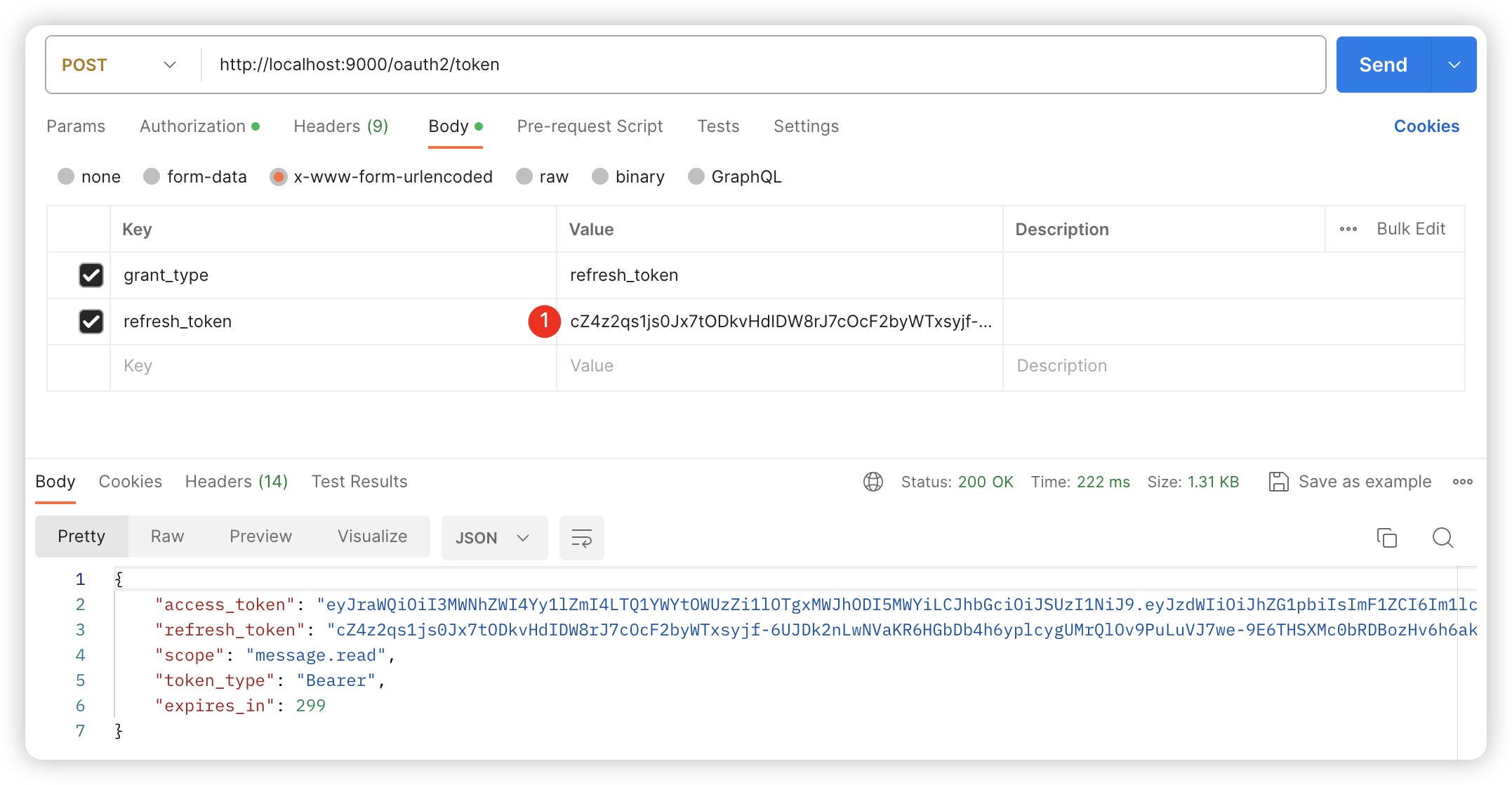
POST /oauth2/token
Body 请求参数
grant_type: refresh_token
refresh_token: cZ4z2qs1js0Jx7tODkvHdIDW8rJ7cOcF2byWTxsyjf-6UJDk2nLwNVaKR6HGbDb4h6yplcygUMrQlOv9PuLuVJ7we-9E6THSXMc0bRDBozHv6h6akNYFmxDkbwIya_Pq请求参数
| 名称 | 位置 | 类型 | 必选 | 说明 |
|---|---|---|---|---|
| body | body | object | 是 | none |
| » grant_type | body | string | 是 | 刷新模式 |
| » refresh_token | body | string | 是 | 刷新令牌 |
cURL代码片段
curl --location 'http://localhost:9000/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic bWVzc2FnaW5nLWNsaWVudDpzZWNyZXQ=' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'refresh_token=cZ4z2qs1js0Jx7tODkvHdIDW8rJ7cOcF2byWTxsyjf-6UJDk2nLwNVaKR6HGbDb4h6yplcygUMrQlOv9PuLuVJ7we-9E6THSXMc0bRDBozHv6h6akNYFmxDkbwIya_Pq'请求结果
{
"access_token": "eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjgwMDQsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjgzMDQsImlhdCI6MTcwODg2ODAwNCwianRpIjoiZGQ1NDQzNTEtMjU5YS00ZTIyLTg2NGEtYTk4ZTdjZTQ2NWQ2In0.Ghnod-DTODgBsLkc6qc8Bpwxt5er6md_c4Bo206nXxopYPLB6nmZ2Bmf0fMWIM666k6KX525rFUNI0fvhUJFPuxSLmcOuck2qS2ZJW-GFEw2D6gbFCGrOJu3YEl78iQ2WIOLeuUW2oASkq4NkfA0PW7OnYC5Nha8nVzfsS96cyvTYKMkrTDmbEqprBSkaV8AKjA1DEgqS6cEBirRxpsS6kJHZIyD-RaOn9950xYM5hYU2-1qfvEzRiQqOKzvZyiRC9tJzwzVm2DlSB3LrFJ7wKTT3K5iPURRb6blwuUwvxVpr0Stw7DKwQ5zCre-4v_Fipek1i_VdhjOmd0m5u6nQg",
"refresh_token": "cZ4z2qs1js0Jx7tODkvHdIDW8rJ7cOcF2byWTxsyjf-6UJDk2nLwNVaKR6HGbDb4h6yplcygUMrQlOv9PuLuVJ7we-9E6THSXMc0bRDBozHv6h6akNYFmxDkbwIya_Pq",
"scope": "message.read",
"token_type": "Bearer",
"expires_in": 299
}④ POST 自省端点
Postman调试
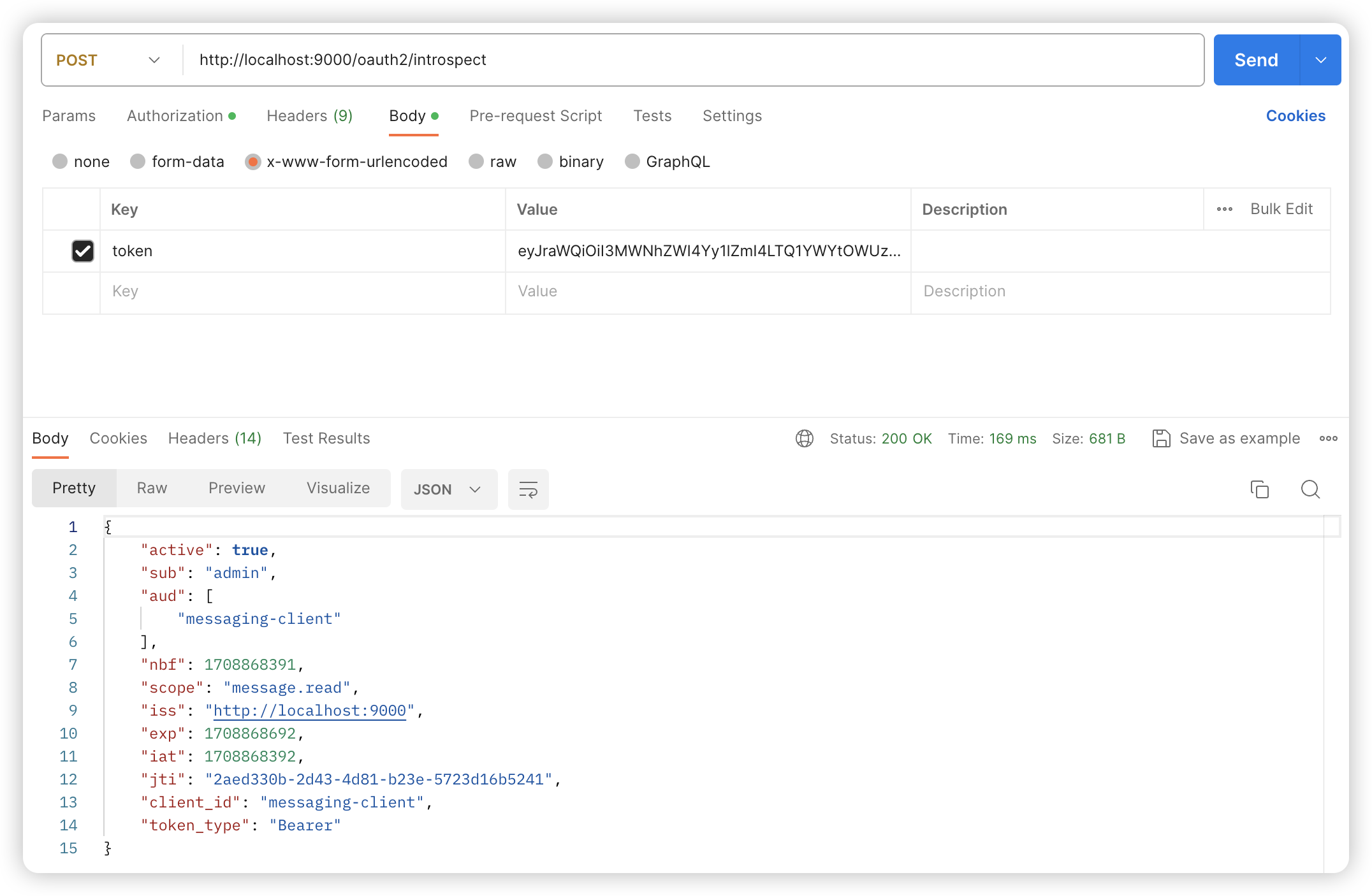
POST /oauth2/introspect
Body 请求参数
token: eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjgzOTEsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4Njg2OTEsImlhdCI6MTcwODg2ODM5MSwianRpIjoiMmFlZDMzMGItMmQ0My00ZDgxLWIyM2UtNTcyM2QxNmI1MjQxIn0.C_hkNaj1W_EEFo2g6IPbinVBNY76aJ0JOl1sBupwQ4hPECfwOEYxIuq0Pd2WMtfdwzTQvP2ylHQbSaytycKuA13VsJVy6SQccc1ugtBJU1kXK9HOKD6S5afHpFyKOFe10PCgGOD_q_0v1tcXdDQRwaZk6XkJ_OGUMygCYMt2N0Jn6AKb2aUVpA3jfysyQIlgvrWYVz7eRolAhJYt07UCnsWfOmrAL-RyW_sxNlODulL37m3i4mENw1Ngad80jr5aURAk60AdI29GTRHu5lobgfLyhNfUYLygAvA5_-Ua2l-TSSPiywREqzkLusF_lNwwR7TzO7brl1hR1r6HwkeUhg#请求参数
| 名称 | 位置 | 类型 | 必选 | 说明 |
|---|---|---|---|---|
| body | body | object | 是 | none |
| » token | body | string | 是 | 令牌 |
cURL代码片段
curl --location 'http://localhost:9000/oauth2/introspect' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic bWVzc2FnaW5nLWNsaWVudDpzZWNyZXQ=' \
--data-urlencode 'token=eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjgzOTEsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4Njg2OTEsImlhdCI6MTcwODg2ODM5MSwianRpIjoiMmFlZDMzMGItMmQ0My00ZDgxLWIyM2UtNTcyM2QxNmI1MjQxIn0.C_hkNaj1W_EEFo2g6IPbinVBNY76aJ0JOl1sBupwQ4hPECfwOEYxIuq0Pd2WMtfdwzTQvP2ylHQbSaytycKuA13VsJVy6SQccc1ugtBJU1kXK9HOKD6S5afHpFyKOFe10PCgGOD_q_0v1tcXdDQRwaZk6XkJ_OGUMygCYMt2N0Jn6AKb2aUVpA3jfysyQIlgvrWYVz7eRolAhJYt07UCnsWfOmrAL-RyW_sxNlODulL37m3i4mENw1Ngad80jr5aURAk60AdI29GTRHu5lobgfLyhNfUYLygAvA5_-Ua2l-TSSPiywREqzkLusF_lNwwR7TzO7brl1hR1r6HwkeUhg'请求结果
{
"active": true,
"sub": "admin",
"aud": [
"messaging-client"
],
"nbf": 1708868391,
"scope": "message.read",
"iss": "http://localhost:9000",
"exp": 1708868692,
"iat": 1708868392,
"jti": "2aed330b-2d43-4d81-b23e-5723d16b5241",
"client_id": "messaging-client",
"token_type": "Bearer"
}⑤ POST 撤掉令牌
Postman调试
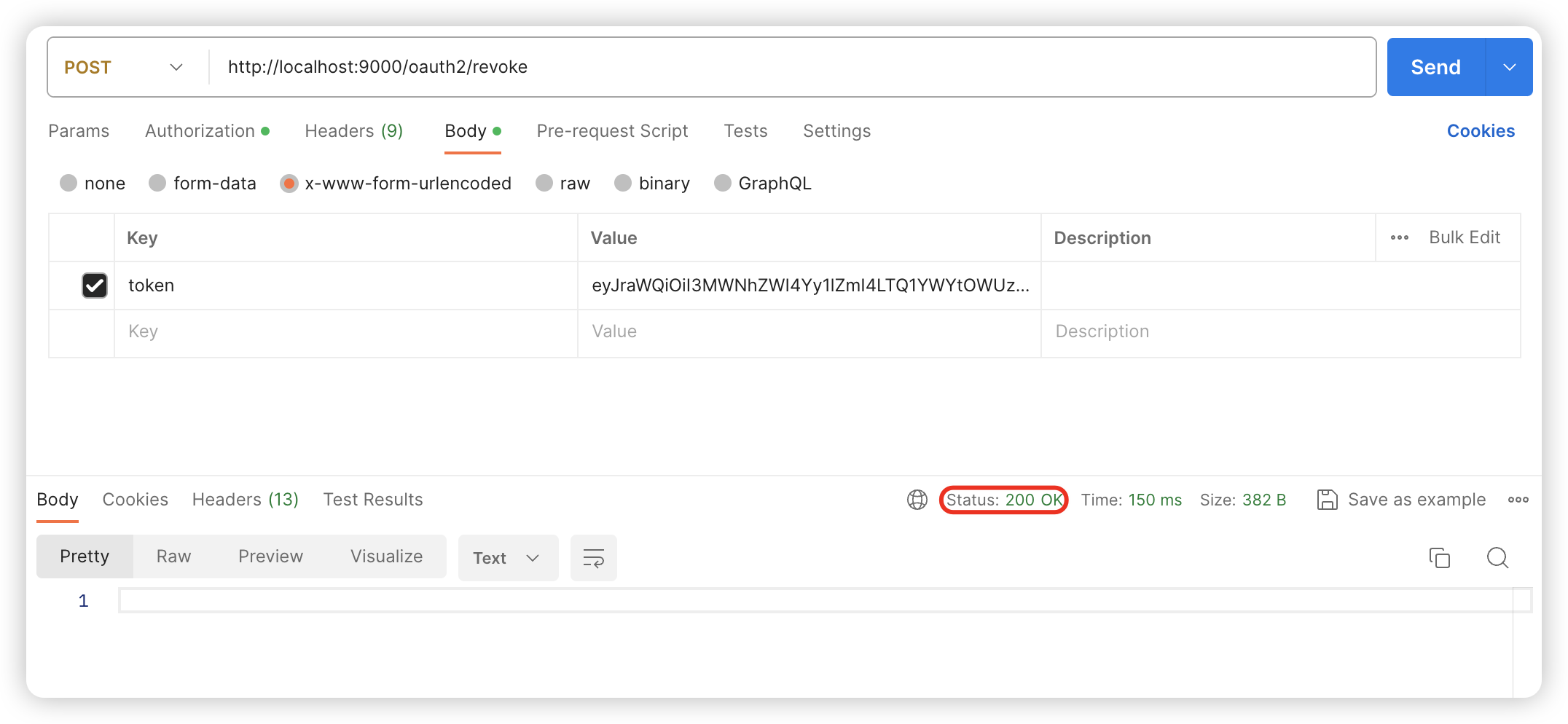
POST /oauth2/revoke
Body 请求参数
token: eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjgzOTEsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4Njg2OTEsImlhdCI6MTcwODg2ODM5MSwianRpIjoiMmFlZDMzMGItMmQ0My00ZDgxLWIyM2UtNTcyM2QxNmI1MjQxIn0.C_hkNaj1W_EEFo2g6IPbinVBNY76aJ0JOl1sBupwQ4hPECfwOEYxIuq0Pd2WMtfdwzTQvP2ylHQbSaytycKuA13VsJVy6SQccc1ugtBJU1kXK9HOKD6S5afHpFyKOFe10PCgGOD_q_0v1tcXdDQRwaZk6XkJ_OGUMygCYMt2N0Jn6AKb2aUVpA3jfysyQIlgvrWYVz7eRolAhJYt07UCnsWfOmrAL-RyW_sxNlODulL37m3i4mENw1Ngad80jr5aURAk60AdI29GTRHu5lobgfLyhNfUYLygAvA5_-Ua2l-TSSPiywREqzkLusF_lNwwR7TzO7brl1hR1r6HwkeUhgcURL代码片段
curl --location 'http://localhost:9000/oauth2/revoke' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Basic bWVzc2FnaW5nLWNsaWVudDpzZWNyZXQ=' \
--data-urlencode 'token=eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4NjgzOTEsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4Njg2OTEsImlhdCI6MTcwODg2ODM5MSwianRpIjoiMmFlZDMzMGItMmQ0My00ZDgxLWIyM2UtNTcyM2QxNmI1MjQxIn0.C_hkNaj1W_EEFo2g6IPbinVBNY76aJ0JOl1sBupwQ4hPECfwOEYxIuq0Pd2WMtfdwzTQvP2ylHQbSaytycKuA13VsJVy6SQccc1ugtBJU1kXK9HOKD6S5afHpFyKOFe10PCgGOD_q_0v1tcXdDQRwaZk6XkJ_OGUMygCYMt2N0Jn6AKb2aUVpA3jfysyQIlgvrWYVz7eRolAhJYt07UCnsWfOmrAL-RyW_sxNlODulL37m3i4mENw1Ngad80jr5aURAk60AdI29GTRHu5lobgfLyhNfUYLygAvA5_-Ua2l-TSSPiywREqzkLusF_lNwwR7TzO7brl1hR1r6HwkeUhg'资源服务器使用
资源服务器搭建
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-oauth2-resource-server</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>测试接口
package com.pigcloud.pigx.admin.web;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
import java.security.Principal;
/**
* @author heyuq
*/
@RestController
public class MessagesController {
@GetMapping
public String principal(Principal principal) {
return principal.getName();
}
@GetMapping("/messages")
public String[] getMessages() {
return new String[] {"Message 1", "Message 2", "Message 3"};
}
}配置文件
指定 token 的签发服务地址(认证服务器地址)
server:
port: 8090
logging:
level:
root: INFO
org.springframework.web: INFO
org.springframework.security: INFO
org.springframework.security.oauth2: INFO
# org.springframework.boot.autoconfigure: DEBUG
spring:
security:
oauth2:
resourceserver:
jwt:
issuer-uri: http://localhost:9000模拟测试
① GET 获取登录用户
Postman调试123
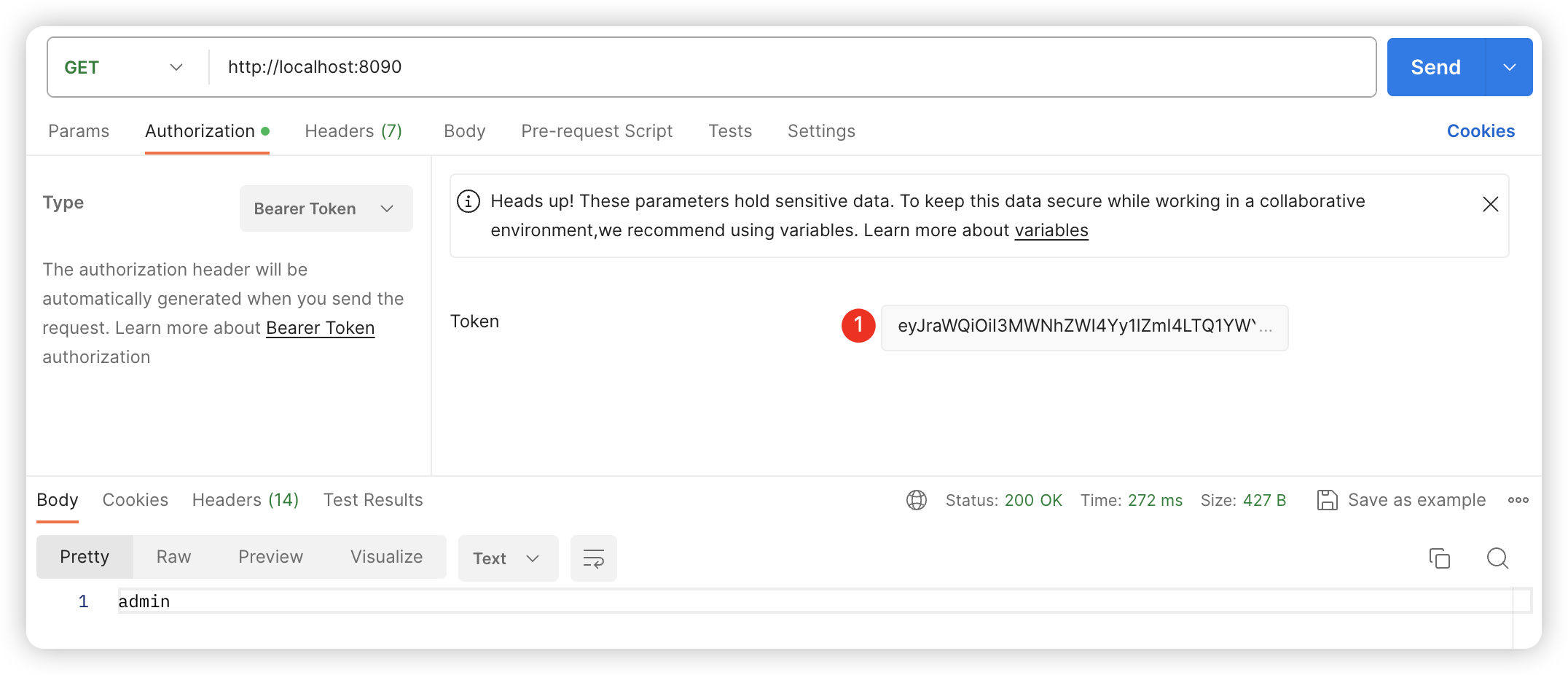
GET /
Headers 请求参数
Authorization: Bearer eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4Njg3MDIsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjkwMDIsImlhdCI6MTcwODg2ODcwMiwianRpIjoiOGIyZjg4OWQtMDk2ZC00MzlmLWJmMWEtNTQ4N2M1MTU5OGI0In0.ik0x6tkYrZiXEYDddPPXSINw-6w2yY3KYapuyX1T2Mdg_zI62sSf4bfoOkSINbelWkbBvkpXsjBGlUky5jzgunObdnAHZxcyRvGyghQ38KWJqmQa6cU9kdwfBgAMsbPDAPysDCjxrrUXOgDjIIuRzM8nH7X1P-lO9Kdq0kkfVPECJ0bYhW981kB7owqj3_TdhGwWc4zaXpnkvE0ghPkadlH2o4zxROivC0t2ifjITORsE6mDTJl2D0zmSsTwAn5xQkckJGCXcHI3URWA7Ea-9NYjHODm2v13VLXQ_LQS-tg4FKDHu6z3-zJFzGe3GITVGe0c0cp-yEYLBy2_7cTTYQcURL代码片段
curl --location 'http://localhost:8090' \
--header 'Authorization: Bearer eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4Njg3MDIsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjkwMDIsImlhdCI6MTcwODg2ODcwMiwianRpIjoiOGIyZjg4OWQtMDk2ZC00MzlmLWJmMWEtNTQ4N2M1MTU5OGI0In0.ik0x6tkYrZiXEYDddPPXSINw-6w2yY3KYapuyX1T2Mdg_zI62sSf4bfoOkSINbelWkbBvkpXsjBGlUky5jzgunObdnAHZxcyRvGyghQ38KWJqmQa6cU9kdwfBgAMsbPDAPysDCjxrrUXOgDjIIuRzM8nH7X1P-lO9Kdq0kkfVPECJ0bYhW981kB7owqj3_TdhGwWc4zaXpnkvE0ghPkadlH2o4zxROivC0t2ifjITORsE6mDTJl2D0zmSsTwAn5xQkckJGCXcHI3URWA7Ea-9NYjHODm2v13VLXQ_LQS-tg4FKDHu6z3-zJFzGe3GITVGe0c0cp-yEYLBy2_7cTTYQ'② GET 获取消息列表
Postman调试
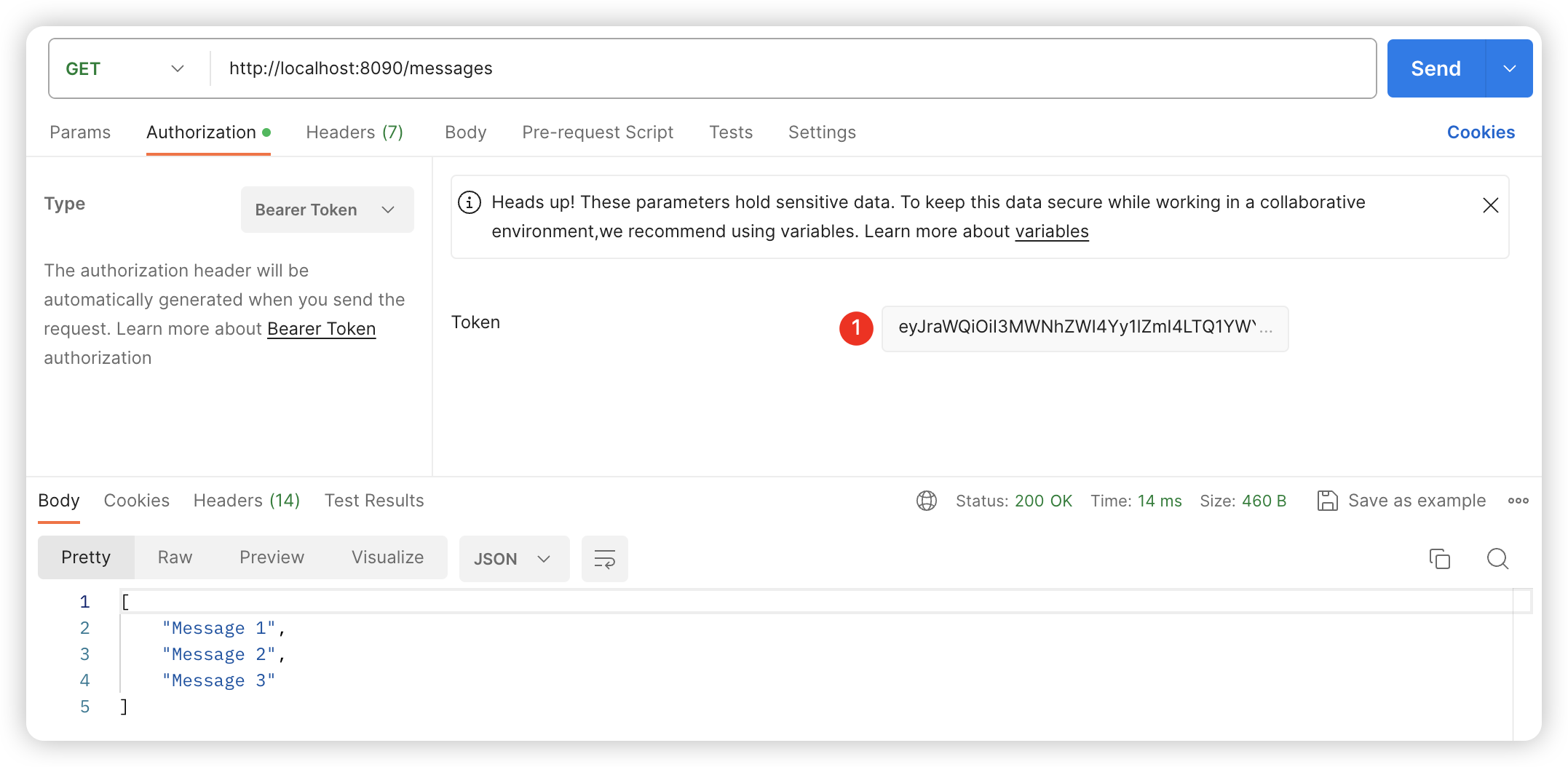
GET /
Headers 请求参数
Authorization: Bearer eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4Njg3MDIsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjkwMDIsImlhdCI6MTcwODg2ODcwMiwianRpIjoiOGIyZjg4OWQtMDk2ZC00MzlmLWJmMWEtNTQ4N2M1MTU5OGI0In0.ik0x6tkYrZiXEYDddPPXSINw-6w2yY3KYapuyX1T2Mdg_zI62sSf4bfoOkSINbelWkbBvkpXsjBGlUky5jzgunObdnAHZxcyRvGyghQ38KWJqmQa6cU9kdwfBgAMsbPDAPysDCjxrrUXOgDjIIuRzM8nH7X1P-lO9Kdq0kkfVPECJ0bYhW981kB7owqj3_TdhGwWc4zaXpnkvE0ghPkadlH2o4zxROivC0t2ifjITORsE6mDTJl2D0zmSsTwAn5xQkckJGCXcHI3URWA7Ea-9NYjHODm2v13VLXQ_LQS-tg4FKDHu6z3-zJFzGe3GITVGe0c0cp-yEYLBy2_7cTTYQcURL代码片段
curl --location 'http://localhost:8090/messages' \
--header 'Authorization: Bearer eyJraWQiOiI3MWNhZWI4Yy1lZmI4LTQ1YWYtOWUzZi1lOTgxMWJhODI5MWYiLCJhbGciOiJSUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImF1ZCI6Im1lc3NhZ2luZy1jbGllbnQiLCJuYmYiOjE3MDg4Njg3MDIsInNjb3BlIjpbIm1lc3NhZ2UucmVhZCJdLCJpc3MiOiJodHRwOi8vbG9jYWxob3N0OjkwMDAiLCJleHAiOjE3MDg4NjkwMDIsImlhdCI6MTcwODg2ODcwMiwianRpIjoiOGIyZjg4OWQtMDk2ZC00MzlmLWJmMWEtNTQ4N2M1MTU5OGI0In0.ik0x6tkYrZiXEYDddPPXSINw-6w2yY3KYapuyX1T2Mdg_zI62sSf4bfoOkSINbelWkbBvkpXsjBGlUky5jzgunObdnAHZxcyRvGyghQ38KWJqmQa6cU9kdwfBgAMsbPDAPysDCjxrrUXOgDjIIuRzM8nH7X1P-lO9Kdq0kkfVPECJ0bYhW981kB7owqj3_TdhGwWc4zaXpnkvE0ghPkadlH2o4zxROivC0t2ifjITORsE6mDTJl2D0zmSsTwAn5xQkckJGCXcHI3URWA7Ea-9NYjHODm2v13VLXQ_LQS-tg4FKDHu6z3-zJFzGe3GITVGe0c0cp-yEYLBy2_7cTTYQ'至此,最少配置的授权服务器就搭建完成了。
参数解释
1. client_id: 客户端的id
2. client_secret: 客户端秘钥
3. redirect_uri:申请授权成功后的回调地址
4. response_type:授权码模式固定参数code
5. code_verifier:一段随机字符串
6. code_challenge:根据指定的加密方式将code_verifier加密后得到的字符串
7. code_challenge_method:加密方式
8. scope:客户端申请的授权范围
9. state:跟随authCode原样返回,防止CSRF攻击
10. grant_type:指定获取token 的方式:
1. refresh_token:刷新token
2. authorization_code:根据授权码模式的授权码获取
3. client_credentials:客户端模式获取